$ 0.075 -0.65%
Request Network (REQ) Rank 906
Request is a decentralized network that allows anyone to request a payment (a Request Invoice) and provide a safe payment method to the receiver. All of the data is stored in a decentralized authentic ledger.
REQ tokens are ERC20 tokens that allow members to participate in the network, create advanced requests and reward several parties who contribute in building the request ecosystem. To the participants, a fee will be charged in REQ and afterward be burned.
| Mkt.Cap | $ 74.81 M | Volume 24H | 15.59 MREQ |
| Market share | 0% | Total Supply | 1000 MREQ |
| Proof type | Open | $ 0.08 | |
| Low | $ 0.07 | High | $ 0.08 |
Network request details
Clear requests
Creates a log resource by using the configuration that you define in the request object. A given BGP VPN can be associated to multiple networks and/or multiple routers. Please refer toDelete minimum bandwidth rulefor more information on the request, response and return codes.

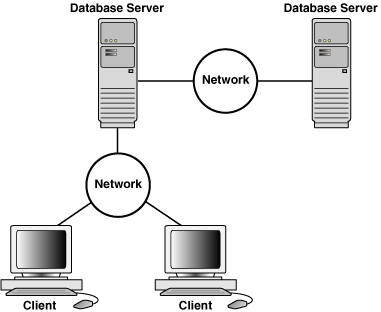
The proxy makes requests on your behalf to websites, servers, and other internet services. In basic web speak, a client makes a request to the server, and the server sends back a response. A proxy server acts as a security barrier between your internal network and the Internet, keeping others on the Internet from accessing information on your internal network. To communicate with an emulator instance behind its virtual router, you need to set up network redirection on the virtual router. Clients can then connect to a specified guest port on the router, while the router directs traffic to/from that port to the emulated device host port.
Filter the list result by the remote IP prefix that is matched by this security group rule. Filter the security group rule list result by the IP protocol. that implies no gateway is associated with the subnet.
A full description of the protocol may be found in our whitepaper. This repository contains all the Request Network developer tools written in TypeScript. Request Network is a decentralized network built on top of Ethereum, which allows anyone, anywhere to request a payment. Typically touted as PayPal 2.0, Request Network is a decentralized payment system that allows anyone to request payments from an individual or organisation. A recipient of a request can then approve payment in a cheap and secure way.
Layer 2 Networking¶
Filter the subnet pool list result by the address scope that is assigned to the subnet pool. As a consequence of this operation, the operation removes the port connecting the router with the subnet from the subnet for the network.
Similarly, web server software can run on any capable computer, and so a laptop or a personal computer can host a web server. Filter the log list result by the ID of resource (e.g security group ID). extension allows users to set tags on their resources.

In principle, any computerized process that can be used or called by another process (particularly remotely, particularly to share a resource) is a server, and the calling process or processes is a client. Thus any general purpose computer connected to a network can host servers. For example, if files on a device are shared by some process, that process is a file server.
Resources that match any tag in this list will be returned. Resources that match all tags in this list will be returned.
Stateful security groups extension (stateful-security-group)¶
- Request acts as a decentralized network that connects payment requests (Request Invoices), and payments.
- Right-click on a resource within the Requests Table, hover overCopy and then select Copy as cURL to copy a string of cURL requests for all resources that have been detected by the Network panel.
- A collection of attributes, such as source and destination ports, source and destination IP addresses, protocol, and IP version.
- Filter the subnet list result by the CIDR of the subnet.
- That means that if you have two instances running concurrently on your machine, each will have its own router and, behind that, each will have an IP address of 10.0.2.15.
Each instance of the emulator runs behind a virtual router/firewall service that isolates it from your development machine network interfaces and settings and from the internet. An emulated device can't see your development machine or other emulator instances on the network. Instead, it sees only that it is connected through Ethernet to a router/firewall. Once you start a server with cy.server(), all requests will be controllable for the remainder of the test. When a new test runs, Cypress will restore the default behavior and remove all routing and stubbing.
Additional resources
If you specify only a subnet ID, OpenStack Networking allocates an available IP from that subnet to the port. A dictionary that enables the application running on the specific host to pass and receive vif port information specific to the networking back-end. The networking API does not define a specific format of this field.
The value of this attribute contains information of the associated port. attributes to floating IPs allowing them to be specified at creation time.

A server connected to the port can send a packet with source address which matches one of the specified allowed address pairs. ) will bypass all rules with source IP address restrictions for all ports which use the same security group. Filter the list result by the human-readable description of the resource. attribute to control the VLAN transparency of the network.

For a complete reference of the API and options, refer to the documentation for each command. By default, Cypress is configured to ignore requests that are used to fetch static content like .js or .html files. This option can be changed by overriding the default whitelisting in the cy.server() options. Filter the log list result by the ID of resource that is the logging target. This is true also in the case where multiple associations are made, and for a router associations of a router connected to the port’s network.
Subnet pools extension (subnetpools)¶

Sorts by the time between the start of the request and the beginning of the response. Select this filter to determine which resource takes the longest time to first byte (TTFB). Sorts by the start time of each network request. This is the default sort, and is the same as sorting by the Start Time option. Request acts as a decentralized network that connects payment requests (Request Invoices), and payments.
Specify a list of subnets in the request body. List of dns name servers associated with the subnet. A subnet can have one or more name servers and host routes. Devices with IP addresses from this subnet, not including the local subnet route, use the host routes.
Networking Agents¶

Lists OpenStack Networking security groups to which the project has access. Filter the RBAC policy list result by the ID of the tenant to which the RBAC policy will be enforced.
The limitation of one IPv4 subnet per router port remains, though a port can contain any number of IPv6 subnets that belong to the same network ID. When you specify an IPv6 subnet, this operation adds the subnet to an existing internal port with same network ID, on the router. If a port with the same network ID does not exist, this operation creates a port on the router for that subnet.







